No AI Generated Content
Introduction - Network Design For A Modern Software Development Company
Get Free Samples Written by our Top-Notch Subject Experts For Taking Online Assignment Help
The SCUSoft.com organization delivers a variety of services and multimedia products; the report analyzes the requirements of that organization to develop their business further. All the latest IT technologies have been implemented through network designing that will easily accommodate the organization load and can handle for the next five years. The report designs network architecture with the latest network devices to fulfil all the requirements. Two routers have been implemented through the design process to transfer information between the two buildings. The design process describes the company headquarters and their sub-network branches such as the software development team, executive management, administration, accounting, marketing, and production departments.
Analysis of user requirements
User requirements analysis delivers the identification, system understanding, and the characteristics over the network; it also defines the development process and performance of the running system to compare servers. The analysis part of this report describes the company requirement through architecture; diagram, where all the network devices have been implemented. The initial requirements have been developed where the number of devices is increased without affecting the security measurement. The user requirements come with the network architecture with the geographical location to process the business requirements. The routers, switches, servers, printers, and workstations are connected accordingly.
Physical Structure
The network architecture has been generated to deliver the packets of information between them. All the structure is the visual representation of network devices where the components are circulated in such a way that can easily describe the data transmission process.
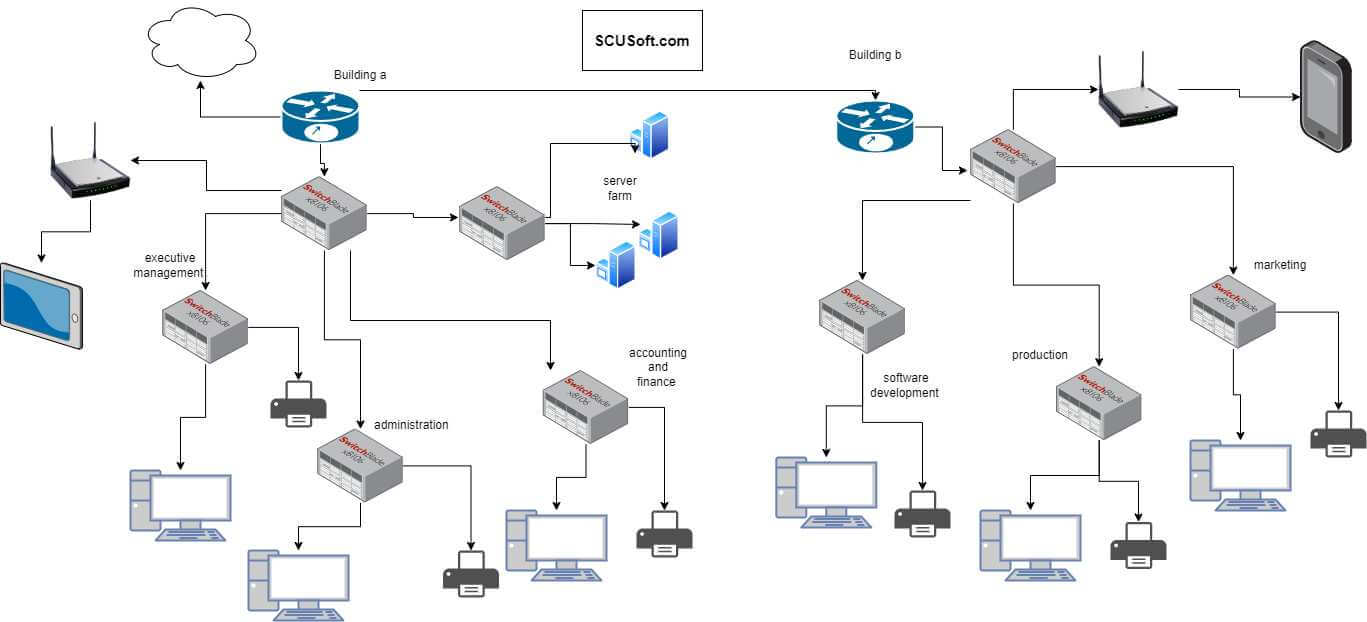
Figure 1: Proposed network architecture
The above figure describes the network architecture where all the organization departments have been visualized. The company buildings are separated with the two edge routers that deliver the information to the workstations. The SCUSoft.com Company has different departments that work at different places in those buildings. All the PCs are representing the workstations and the printers are connected accordingly (Yang and Xu, 2020). The switches are the junction point of communication and it helps to communicate with other departments. The physical structure refers to the above network architecture and the methods will be implemented to connect the network devices accordingly (Al-Khaffaf and Al-Hamiri, 2021). The wired connection between the networks describes the hierarchical network architecture that will be implemented for the complete network layout.
Purpose of business network
The network analysis part delivers the communication process and the successful packet transmission or replies from the other devices. The purpose of business networks decibels the requirements of the network architecture. It provides the ability to collaborate with other business requirements. The analysis of a business network improves the production and marketing of that organization and provides opportunities to compete with other business owners. The proper communication process with successful information transmission has been described through this analysis (Paramonov et al. 2022).
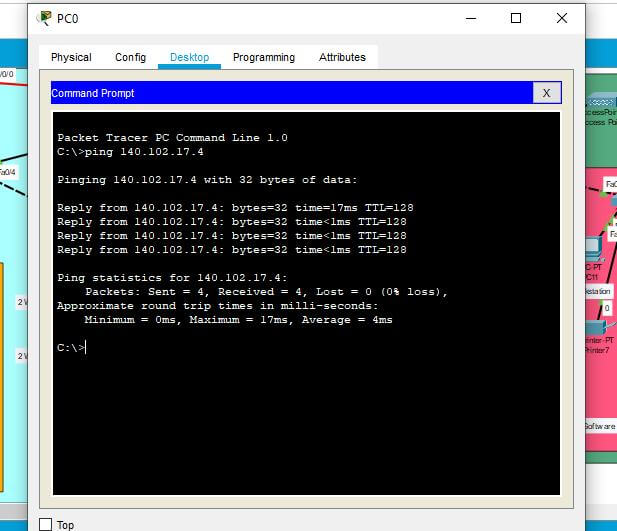
Figure 2: successful pinging test for Pc
The above figure describes the pinging test where PCs reply to the other PCs. The network configuration occurs with a link-local address and delivers a specific IP address configuration. The pinging test defines the reply from the other PCs and helps to communicate with each other. The purpose of this test is to get updated information from the other departments that will keep the business running. The multimedia and other services will be easily accessible through this network analysis (Al-Khaffaf and Al-Hamiri, 2021).
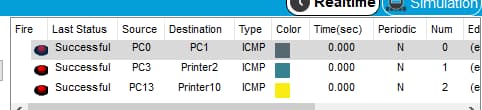
Figure 3: successful packet transmission
The above figure shows the successful packet transmission between the network devices, where communication has been described through the split devices. Influenced from the view of Al-Khaffaf and Al-Hamiri (2021), all the split subnetwork branches are connected and they can easily transfer packets to communicate. The successful packet transmission differs from the existing function and delivers the capabilities over the business requirements.
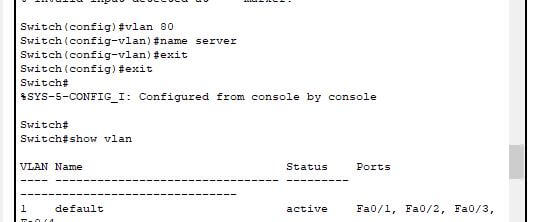
Figure 4: VLAN connection
The above figure describes the virtual LAN configuration through the network switches that help to place different interfaces with a broadcasting system. The local area network connection delivers the overall network architecture and the process describes the hierarchical network analysis over the split network sub-branches. VLAN works like an Ethernet LAN and spreads over multiple switches (Cirella et al. 2021).
Network topology and IP addressing schemes have been implemented through the networking devices that describe the arrangement of these components. All the tests are implemented according to their respective IP address, where the main headquarters of this company communicates with all the sub-network departments.
Used Hardware
In the "Ethernet network protocol," the hardware device helps to interact and communicate with the other network devices. The hardware components come with all the network device configurations. The used hardware devices in this network design process are routers, switches, PCs, servers, and printers. All these components have been assigned with a specific link-local address that helps to transfer packets in a specific route. The proper implementation process describes the specific routes with pocket transmission process between the company's different branches. The network devices such as the routers help to provide the routes for packet transmission. The switches provide the communication process and the workstations are designed with organization PCs.
Used Software
The network architecture has been designed with the "cisco packet tracer" software platform, where all the departments and combination network devices are arranged accordingly (Sato et al. 2019). The illustration helps to analyze the complexity of the overall network design. The software part of this networking process initiates the network devices and programmed or controlled them centrally. The IT team can easily analyze the business requirements and can manage the entire network consistency with the integrity of data. A well-developed network architecture secures the data transmission process and reduces the risk factors from the overall network. The hierarchical network design delivers the complete configuration of the organization's departments.
Network layout
The network layout comes with the complete network architecture where all the network components have been implemented to communicate with each other. The network topology with physical configuration has been implemented where both mesh loop analyses can be implemented. The network devices with geographical representation describe the complete networking and analysis (Szewczyk and Macdonald, 2017).
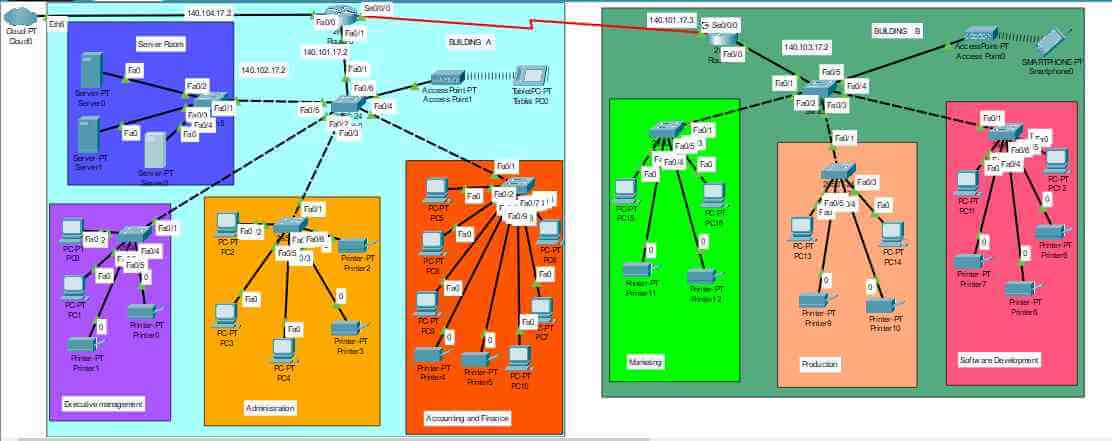
Figure 5: Complete network architecture
The above figure describes the complete network architecture where all the network components have been designed accordingly. The edge routers represent the different buildings in that organization and those are connected with the different subnetwork departments. All the departments are allocated accordingly, where the executive management, administration, accounting has been located in building A. However, the software development, marketing, and production department has been located in building B. All the departments have different printers and workstations that have been configured accordingly. The edge router in building A has been connected to the cloud, which can easily access the internet to transfer the data. Both the buildings have wireless connections that easily transmit data over the internet. Wireless connection has been implemented with an access point to connect with remote devices.
The 2811 router series has been implemented with the 2960 PT switches to connect the workstations and printers.
IPv4 addressing plan for network devices
IPv4 addressing occurs with a 32-bit number addressing that delivers a specific route to transmit data from the one network to another. The IP addressing scheme occurs with decimal digits where each 8 bit represents the bytes of IPv4 addresses. The decimal IP addresses have been implemented and that is represented with a dotted decimal format. The three types of IPv4 addressing are
- Unicast
- Broadcast
- And multicast rerouting
The IP addresses occur with the device IP addresses, with the subnet mask and default IP. all the network devices have a specific IP address along with their subnet mask and default IP address. The subnet mask identifies each 32-bit number along with the host network address and device network address. The device addresses are configured along with the default gateway where the last decimal digit is 1, which represents the specific routes to transmit data.
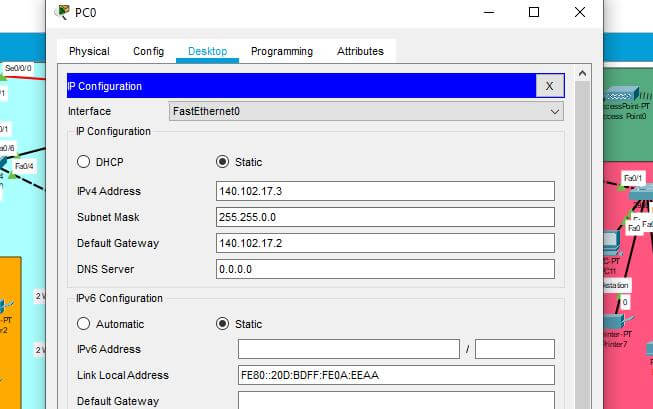
Figure 6: IPv4 addressing for PCs
The above image describes the IP addressing scheme in network PCs, where the default gateway is 141.111.17.1 and the subnet mask is 255.255.0.0 specifies the host address and the device address. All the PCs are configured accordingly to transfer data between the other departmental branches. The IP addressing schemes occur with the device link-local address to describe their route of data transmission. Using the IP addressing in the desktop of that helps PCs the addresses can be configured respectively (Guo et al. 2020).
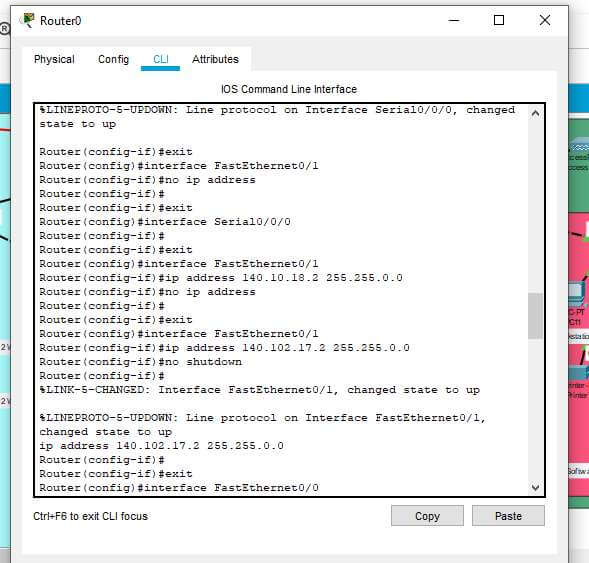
Figure 7: IPv4 addressing for routers
The above image describes the IPv4 addressing in the routers that possesses the communication in a specific manner. The router's IP configuration delivers the complete configuration in its CLI section. In the command section, the IP configuration can be possible by enabling the routers with terminal configuration. The routers are configured with IP 141.110.20.1 while the serial ports are connected with this IP address. The Ethernet ports are connected with the default IP addresses schemes. Using no shut process the routers are configured accordingly where all the processes are described through the above figure.
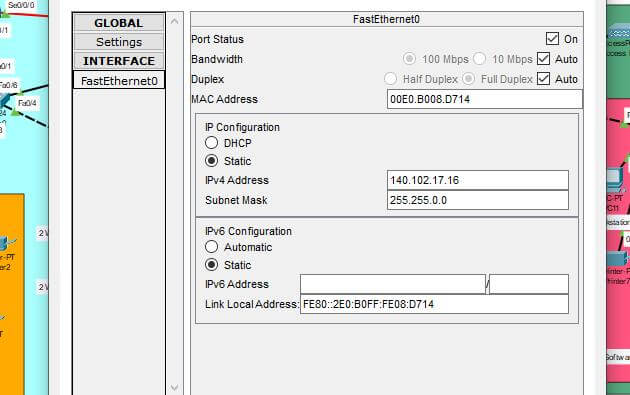
Figure 8: IPv4 addressing for printers
The above image describes the IP addressing in printers where the static IPv4 address in the printer is 141.111.17.0/16 with the 16-bit decimal codes. The process of subnet mask will be automatically generated by addressing the IPv4 addresses.
The IP address scheme delivers the process of route specification and the security process has been implemented through the networking.
Conclusion
The business network describes the requirements in the network architecture that provides the ability to collaborate with other business requirements. The analysis of a business network improves the production and marketing of that organization and provides opportunities to compete with other business owners. As a business grows, so do its requirements. Maintaining a larger database for clients ensures that the business can bring in more funds for the organization. This process ensures that the business maintains stability even while growing. This process requires the involvement of a high-functioning network architecture that can ensure the organization can keep up with its customers and other competing businesses. This is an important factor that is often overlooked. Organizations primarily intend to provide support to their members and clients. Hence there is a high chance of gaining tunnel vision and organizations keep on piling the procedures on to provide them with high-quality service. However, in the case of competing services, there also are opportunities that should not be entirely overlooked.
The report concludes that the network requirements will be further improved without affecting the network security. The report delivers the hierarchical network architecture to convert the business analysis with high marketing and production rates. The base architecture delivers the complete process of an overall network system that can transmit data through a specific route with different network devices. The process of each network analysis comes with structuring the different departments through hardware devices. Cisco software platform has further increased the implementation process through the packet transferring in the different sub-network branches. The implementation process increases the network security with each other process of IP addressing and all the PCs are configured accordingly to transfer data between the other departmental branches. The IP addressing schemes occur with the device link-local address to describe their route of data transmission.
Based on the work that has been completed in this study, there are several opportunities for upgrading the output of the processes in the organization. The overall procedure of enhancing the product selling can always be enhanced. This is even more relevant in the case of organizations that are primarily involved in selling products and providing services to their clients. Thus the members of such an organization must look for every opportunity to develop their system in a manner that can provide superior support to their clients.
References
Al-Khaffaf, D. And Al-Hamiri, M., 2021. Performance evaluation of campus network involving VLAN and broadband multimedia wireless networks using OPNET modeler. Telkomnika, 19(5), pp. 1490-1497.
Guo, C., Gong, C., Guo, J., Wei, Z., Han, Y. And Sher, Z.K., 2020. Software-Defined Space-Air-Ground Integrated Network Architecture with the Multi-Layer Satellite Backbone Network. Computers, Materials, & Continua, 64(1), pp. 527-540.
Makeri, Y.A., Cirella, G.T., Galas, F.J., Jadah, H.M. And Adeniran, A.O., 2021. Network Performance through Virtual Local Area Network (VLAN) Implementation & Enforcement on Network Security for Enterprise. International Journal of Advanced Networking and Applications, 12(6), pp. 4750-4762.
Paramonov, A., Muthanna, A., Aboulola, O.I., Elgendy, I.A., Alharbey, R., Tonkikh, E. And Koucheryavy, A., 2020. Beyond 5G Network Architecture Study: Fractal Properties of Access Network. Applied Sciences, 10(20), pp. 7191.
Sato, R., Yamada, K., Shinozuka, Y., Ochiai, H. And Onda, K., 2019. Gas-filled urachal abscess with a pinging sound in a heifer calf. Veterinární Medicína, 64(8), pp. 362-366.
Szewczyk, P. And Macdonald, R., 2017. BROADBAND ROUTER SECURITY: HISTORY, CHALLENGES AND FUTURE IMPLICATIONS. The Journal of Digital Forensics, Security and Law : JDFSL, 12(4), pp. 55-73.
Yang, G. And Xu, M., 2020. Research on Network Architecture and Communication Protocol of Network Virtual Reality Based on Image Rendering. IOP Conference Series.Materials Science and Engineering, 740(1),.

